Shadow Protect Enable Lan Communications
a.k.a. How to create an XP Firewall Exception
GPO in SBS
by Andy Goodman [SBS-MVP]
So as you may know I have been working with imaging
products
and have pretty much settled on Storage
Craft's products.
Well I hit a road block the other day trying to control the desktop
versions of
Shadow Protect from the
Shadow
Protect Server Console.
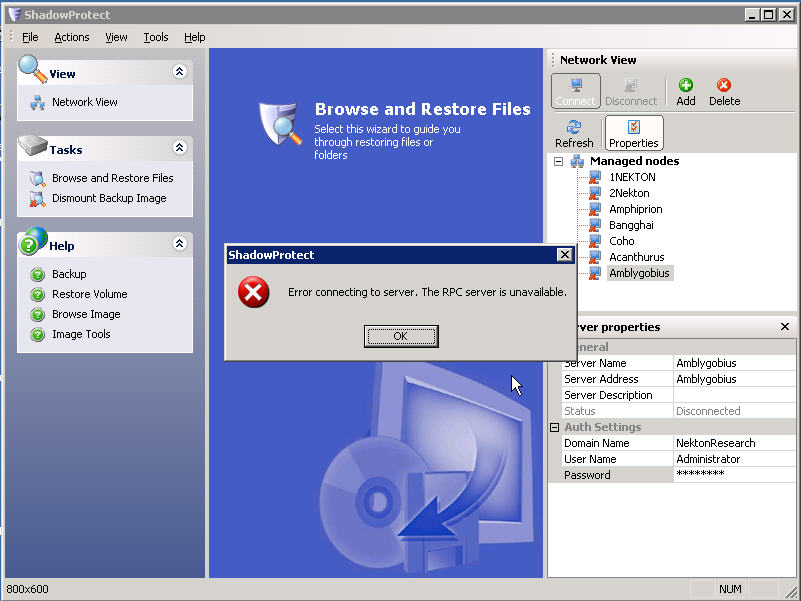
I talked to their support department and they gave me the link to a really
convoluted MSDN paper on configuring dcomm which is not for the faint of heart.
I started implementing that solution and it was not going well and I figured
there had to
be a simpler way.
Let me share with you the easy way to get this to work and
in the process you can learn
how to create a GPO to allow a program to communicate over your lan.
Also let me point out that there is firewall section in
the default domain policy,
but this is an SBS network and we don't want to mess with the default policies
as we never know when a wizard or a hot fix may come along and reset them.
If we build our own policies we know they will be there until we delete them.
So without further delay, lets build our own GPO
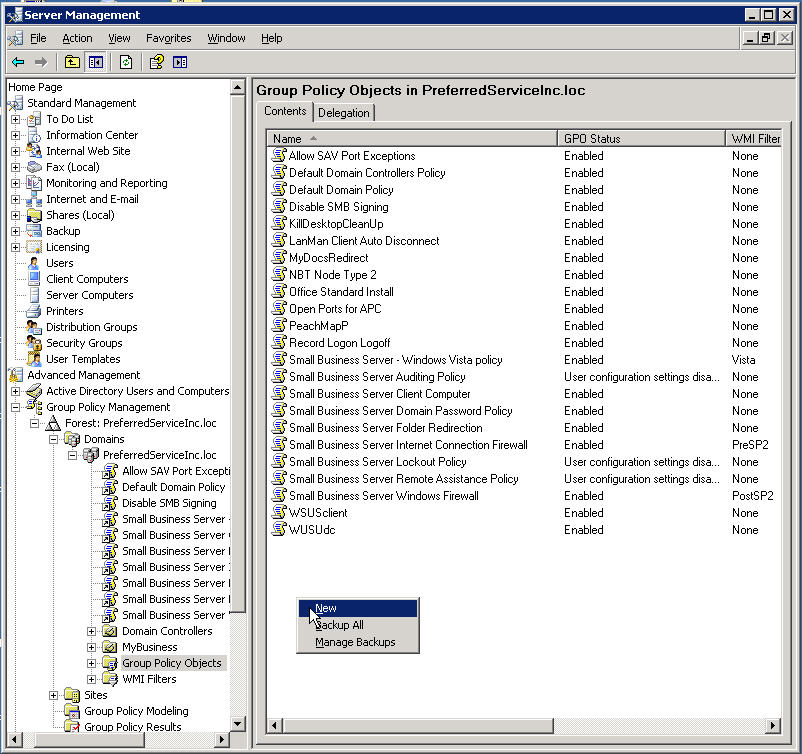
Open the SBS Server Management Console
In the Advanced Management section open Group Policy Management
Drill down through Forrest, Domains, {YourDomainName} and click Group Policy
Objects
Right click in the right hand pane and choose New
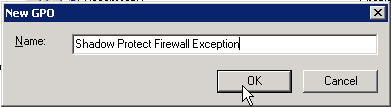
Lets give our new GPO a name that describes what is does
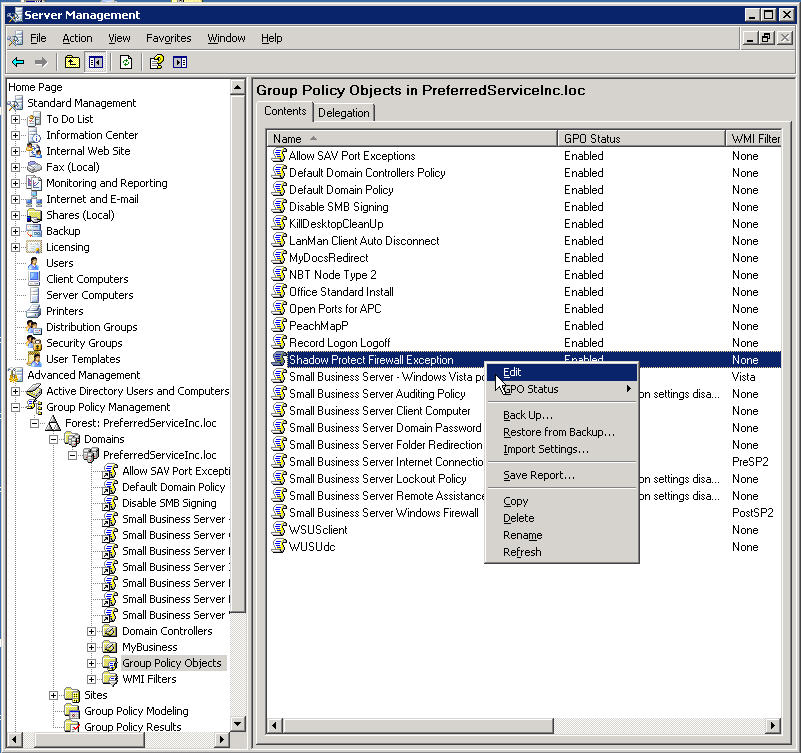
Now right click on our new GPO and choose Edit
Article Update see the ADM Template offered by Bob Haley
Drill down in the Computer Configuration section through
Administrative Templates, Network, Network Connections
keep going past Windows Firewall and click on Domain Profile
Now right click on Allow local program exceptions and choose properties
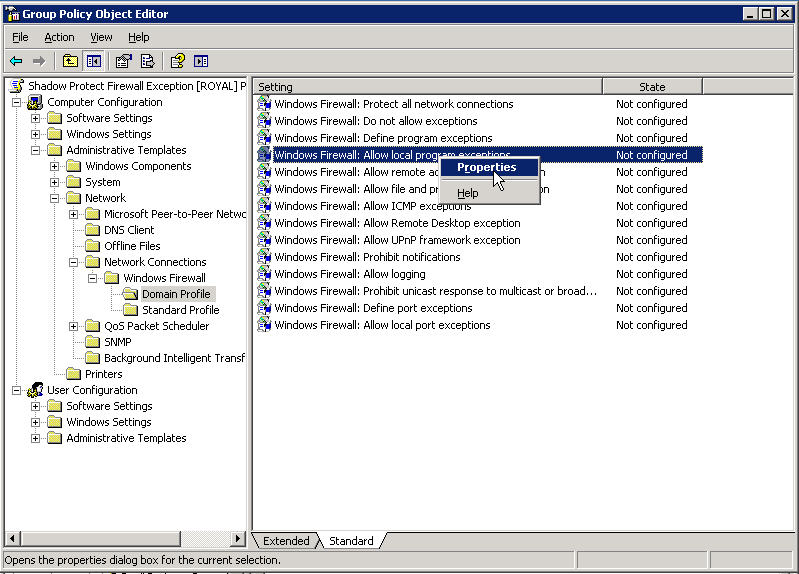
Click Enabled and then OK
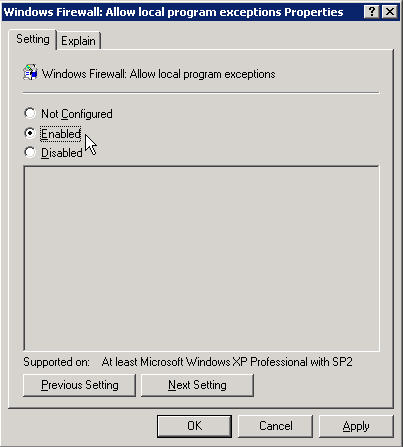
Now right click on Define program exceptions and choose properties
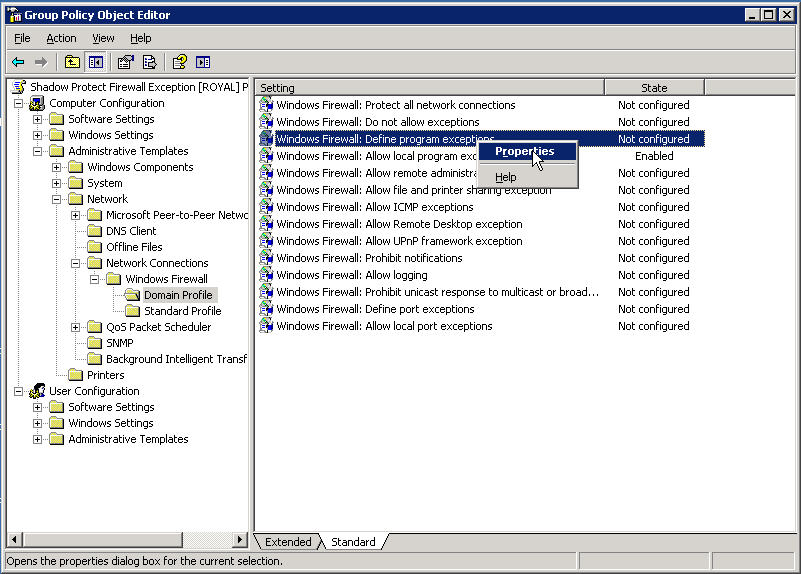
Click on Enabled and then click the Show button
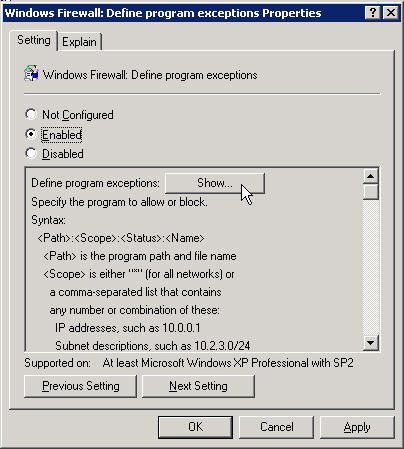
In the Show Contents window click the Add button
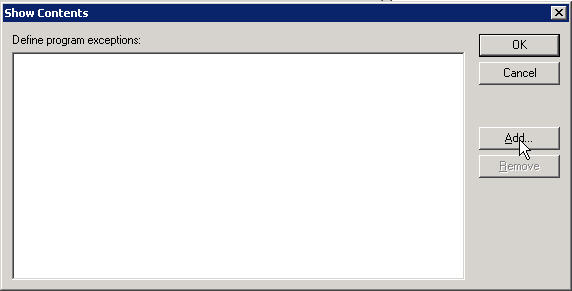
In the Add Item window enter the next line exactly (if you are doing another program enter be it's path)
%ProgramFiles%\StorageCraft\ShadowProtect\ShadowProtectSvc.exe:*:Enabled:Shadow Protect Service
And then click OK
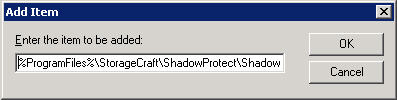
Now click OK in the Show Contents window
And once again in the Define program exceptions window
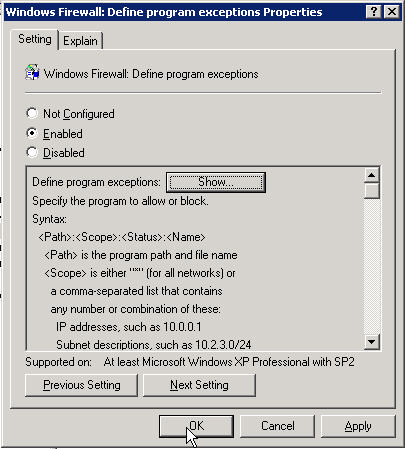
Now you can close the Group Policy Object Editor
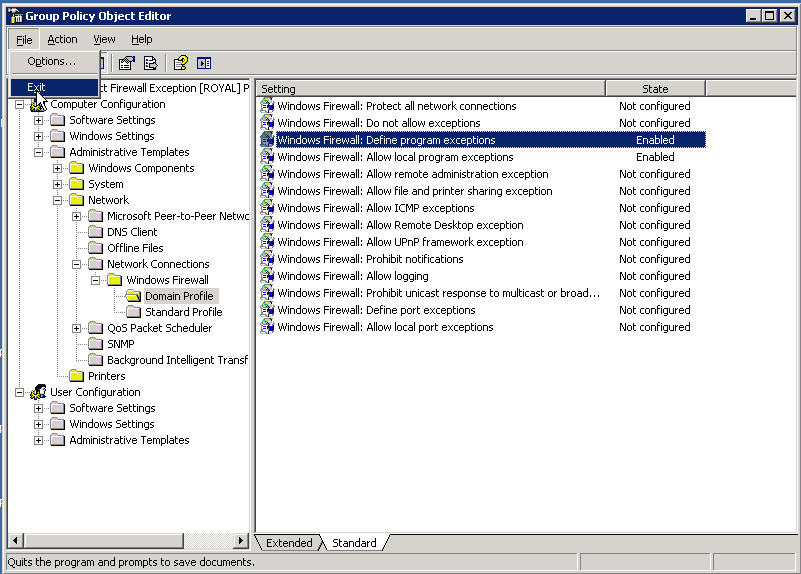
Now go up the tree a little bit to {YourDomainName} and right click on it, choose Link an Exisiting GPO
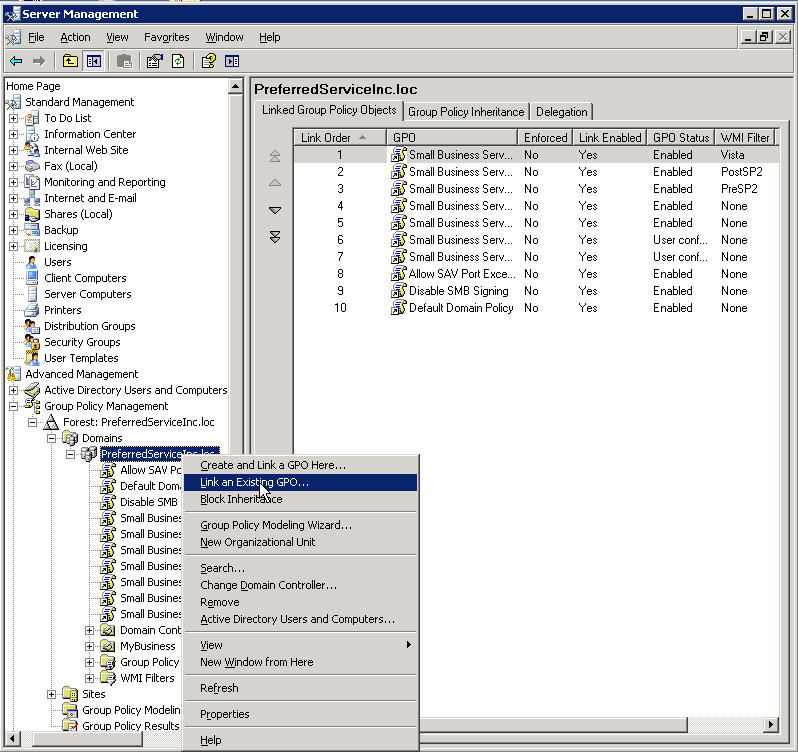
Select our new GPO and click OK
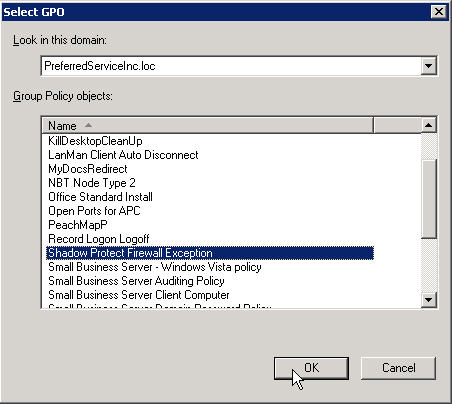
Now we need a little housekeeping
The default Domain Policy should always be the last on the list
So select it and then click the down arrow until it is at the bottom
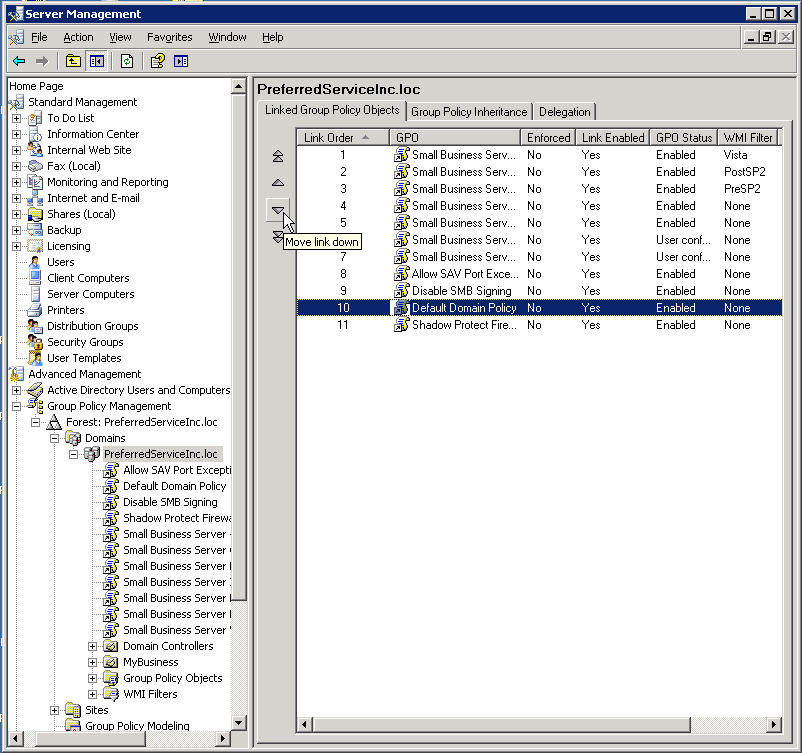
Ah that is much better, now you can close SBS management Console
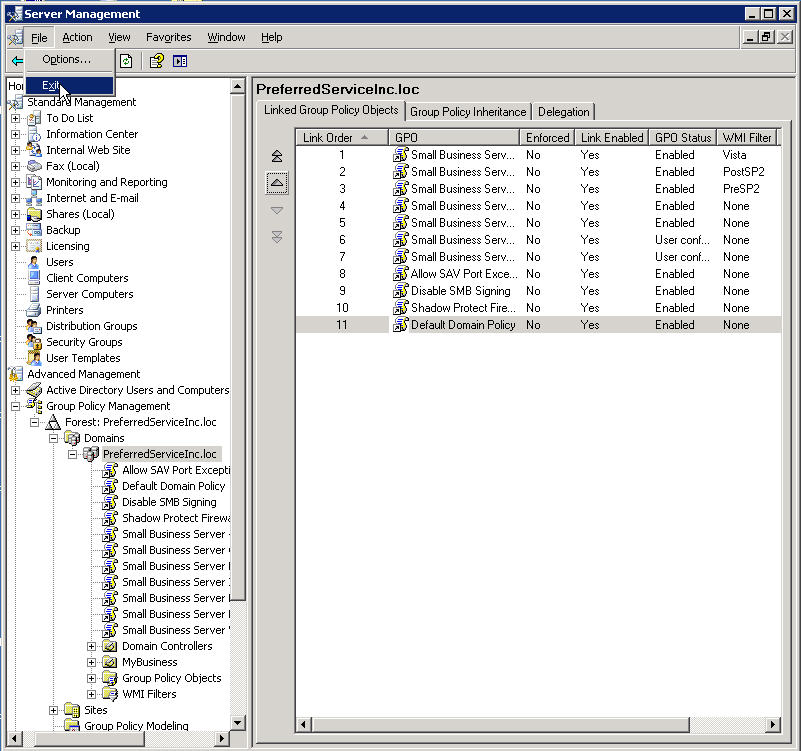
You could wait around for hours for this to take effect,
but if you have no patience like me
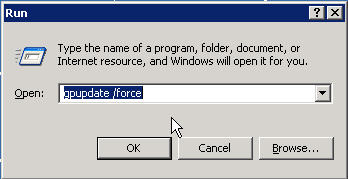
Click Start, Run and type gpupdate /force
in the open box and click OK
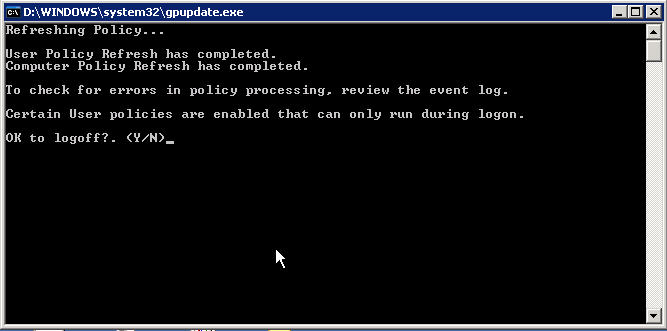
You will need to let it log you off the server, so type a Y and hit <Enter>
You will also need to run this same command on the
workstations, the only difference is
they will require a reboot instead of a log off.
But after the reboot you can manage the workstations from the Shadow Protect Server Console
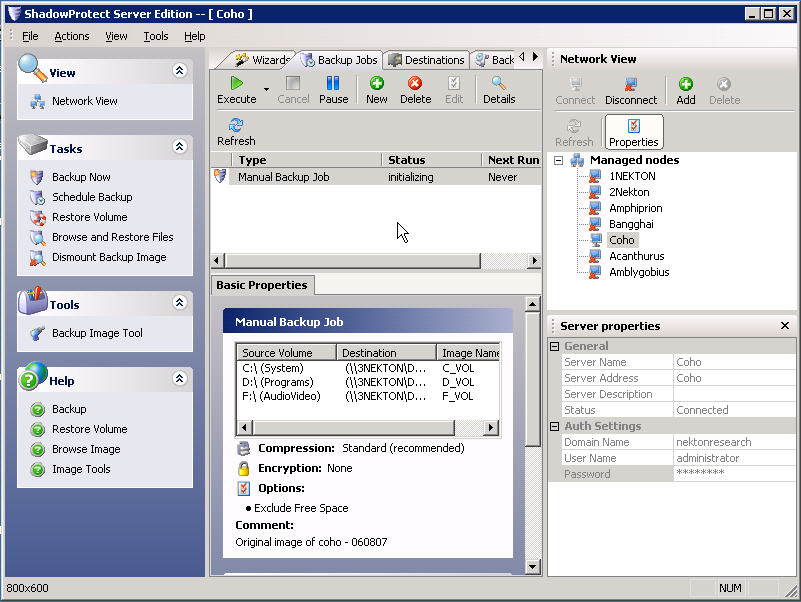
So until next time always remember
SBS ROCKS !
And what a great community, I am so glad to be a part of it
After reading this article, fellow
SMBTN member Bob Haley
of CADDTECH took the time to build an ADM Template
to make this process easier for you.
Here is his note to me,
Andy
You may want to use this custom .adm file to set the exceptions in your XP firewalls for ShadowProtect.
You can publish the file on your web site if you like it.
I am sending you a .txt file - just rename it to shadowprotect.adm
To install:
Just copy the .adm file into c:\windows\inf on the PDC server.(such as sbs 2003)
Create a new GPO, edit, go to Computer Configuration, Administrative Templates, right click, and Add new template, and add the shadowprotect template.
There are only three policies, the two you mentioned in your article plus a third that could be "disabled"
to gray out the "Don't Allow Exceptions" check box on the firewall. This will keep local admins from blocking your policies.
The advantage - this file is portable from installation to installation, and you don't have to remember to type that gosh awful string - it gets placed in the box automatically when you enable the policy.
Enjoy.
Bob Haley, MCSA, Microsoft Small Business Specialist CADDTECH Consulting
Thank You Bob,
Here are the contents of the ADM file, just copy the green text below into a new file in notepad and save it as shadowprotect.adm
Of course I have to say for Bob's sake as well as my own,
USE AT YOUR OWN RISK!
CLASS MACHINE
;comment
CATEGORY "Add Shadow Protect Exception"
POLICY !!WF_EnableShield_Name
#if version >= 4
SUPPORTED !!SUPPORTED_WindowsXPSP2
#endif
EXPLAIN !!WF_EnableShield_Help
KEYNAME "SOFTWARE\Policies\Microsoft\WindowsFirewall\DomainProfile"
VALUENAME "DoNotAllowExceptions"
VALUEON NUMERIC 1
VALUEOFF NUMERIC 0
END POLICY
POLICY !!WF_AllowedProgramsLocal_Name
#if version >= 4
SUPPORTED !!SUPPORTED_WindowsXPSP2
#endif
EXPLAIN !!WF_AllowedProgramsLocal_Help
KEYNAME "SOFTWARE\Policies\Microsoft\WindowsFirewall\DomainProfile\AuthorizedApplications"
VALUENAME "AllowUserPrefMerge"
VALUEON NUMERIC 1
VALUEOFF NUMERIC 0
END POLICY
POLICY "Add Shadow Protect Exception"
#if version >= 4
SUPPORTED !!SUPPORTED_WindowsXPSP2
#endif
EXPLAIN !!ShadowProtectException_Help
KEYNAME "SOFTWARE\Policies\Microsoft\WindowsFirewall\DomainProfile\AuthorizedApplications\List"
PART "Add Program" EDITTEXT
VALUENAME "%ProgramFiles%\StorageCraft\ShadowProtect\ShadowProtectSvc.exe:*:Enabled:Shadow
Protect Service"
DEFAULT "%ProgramFiles%\StorageCraft\ShadowProtect\ShadowProtectSvc.exe:*:Enabled:Shadow
Protect Service"
END PART
END POLICY
END CATEGORY ;add shadow protect exception
[strings]
SUPPORTED_WindowsXPSP2="At least Microsoft Windows XP Professional with SP2"
WF_OpenPorts_Show1="Define port exceptions:"
WF_AllowedProgramsLocal_Help="Allows administrators to use the Windows Firewall
component in Control Panel to define a local program exceptions list. Windows
Firewall uses two program exceptions lists; the other is defined by the "Windows
Firewall: Define program exceptions" policy setting.\n\nIf you enable this
policy setting, the Windows Firewall component in Control Panel allows
administrators to define a local program exceptions list.\n\nIf you disable this
policy setting, the Windows Firewall component in Control Panel does not allow
administrators to define a local program exceptions list.\n\nIf you do not
configure this policy setting, the ability of administrators to define a local
program exceptions list depends on the configuration of the "Windows Firewall:
Define program exceptions" policy setting. If that setting is not configured,
administrators can define a local program exceptions list. If it is enabled or
disabled, administrators cannot define a local program
exceptions list."
WF_AllowedProgramsLocal_Name="Windows Firewall: Allow local program exceptions"
WF_EnableShield_Name="Windows Firewall: Do not allow exceptions"
WF_EnableShield_Help="Specifies that Windows Firewall blocks all unsolicited
incoming messages. This policy setting overrides all other Windows Firewall
policy settings that allow such messages.\n\nIf you enable this policy setting,
in the Windows Firewall component of Control Panel, the "Don't allow exceptions"
check box is selected and administrators cannot clear it. You should also enable
the "Windows Firewall: Protect all network connections" policy setting;
otherwise, administrators who log on locally can work around the "Windows
Firewall: Do not allow exceptions" policy setting by turning off the
firewall.\n\nIf you disable this policy setting, Windows Firewall applies other
policy settings that allow unsolicited incoming messages. In the Windows
Firewall component of Control Panel, the "Don't allow exceptions" check box is
cleared and administrators cannot select it.\n\nIf you do not configure this
policy setting, Windows Firewall applies other policy settings that allow unsolicited incoming messages. In the Windows Firewall component of Control
Panel, the "Don't allow exceptions" check box is cleared by default, but
administrators can change it."
ShadowProtectException_Help="If enabled, the exception for ShadowProtect will be
added to the Windows Firewall list of exceptions."